A digital signature is a cryptographic methodology used to make sure the validity and integrity of digital knowledge. We are able to consider it as a digital equal of a conventional handwritten signature, however with extra complexity and safety.
Merely put, a digital signature is a code linked to a message or doc. As soon as shaped, the code verifies that the communication was not tampered with on its journey from sender to receiver.
Though the notion of using cryptography to safe communications stretches again to historical occasions, digital signature methods turned doable within the Nineteen Seventies, owing to the arrival of Public-Key Cryptography (PKC).
To know what a digital signature is in bitcoin and the way it works, we should first grasp the basics of hash operate and public-key cryptography.
Key Takeaways
- Digital signatures in Bitcoin are used to show the authenticity of transactions and the possession of the funds being transferred.
- Bitcoin makes use of Elliptic Curve Digital Signature Algorithm (ECDSA) to generate a singular signature for every transaction.
- The signature is included within the transaction knowledge and verified by different nodes within the community earlier than the transaction could be added to the blockchain.
- Digital signatures assist to make sure that a transaction has not been tampered with and was initiated by the proprietor of the personal key related to the general public handle used within the transaction.
- Digital signatures in Bitcoin are a vital facet of public key cryptography, a basic expertise underlying the safety of the Bitcoin community.
What Is a Digital Signature?
A digital signature is a mathematical approach used to validate the authenticity and integrity of a message or a digital doc. It’s an uneven encryption approach that makes use of a personal key to encrypt a hash of the doc and an identical public key to decrypt it.
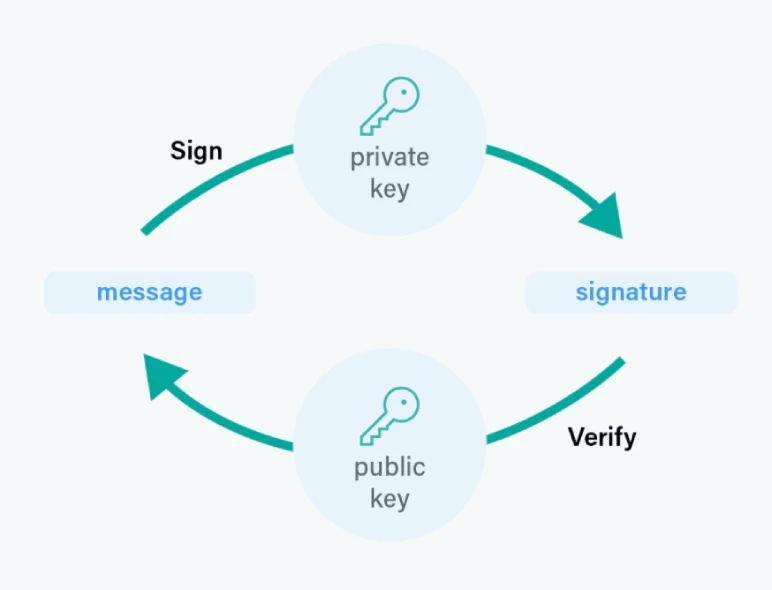
This permits the doc’s recipient to verify that the knowledge in digital messages has not been tampered with and was despatched by the acknowledged sender. By encrypting your complete message with the recipient’s public key, we are able to be certain that solely the recipient, who’s in possession of the corresponding personal key, can learn the message. We are able to additionally confirm the consumer’s identification utilizing the general public key and test it in opposition to a certificates authority.
Digital signatures are extensively employed in digital communications and on-line banking to guarantee the validity and integrity of the knowledge being transmitted.
Hash Perform
Hashing is a key part of the digital signature system. The Cybersecurity and Infrastructure Safety Company (CISA) defines a hash operate as:
A set-length string of numbers and letters generated from a mathematical algorithm and an arbitrarily sized file akin to an e-mail, doc, image, or different sort of knowledge. This generated string is exclusive to the file being hashed and is a one-way operate—a computed hash can’t be reversed to search out different recordsdata which will generate the identical hash worth.
A hash operate can be utilized to transform an arbitrary enter into the correct format. When paired with cryptography, cryptographic hash capabilities can present a hash worth (digest) that serves as a singular digital fingerprint. Which means each modification within the enter knowledge (message) ends in a wholly new final result (hash worth). Because of this, cryptographic hash capabilities are generally utilized to validate digital knowledge.
Public-Key Cryptography (PKC)
Public-key cryptography (PKC) is a cryptographic approach that employs a public key and a personal key. The 2 keys have a mathematical relationship and could be utilized for knowledge encryption in addition to e-signatures.
PKC is a safer encryption expertise than symmetric encryption algorithms. In contrast to prior methods, which used the identical key to encrypt and decrypt knowledge, PKC permits for knowledge encryption with the general public key and knowledge decryption with the related personal key.
Moreover, the PKC methodology can be utilized to generate an e-signature. In essence, the method includes hashing a message (or digital knowledge) together with the signer’s personal key. The recipient of the message can then use the signer’s public key to validate the signature.
Digital signatures could require encryption in some circumstances, though this isn’t all the time the case. For instance, the Bitcoin blockchain employs PKC and digital signatures; nonetheless, opposite to fashionable perception, no encryption is concerned. Bitcoin makes use of the so-called Elliptic Curve Digital Signature Algorithm (ECDSA) to authenticate transactions.
Quick Truth
1. The primary digital signature algorithm referred to as the “Diffie-Hellman Key Alternate,” was proposed by Whitfield Diffie and Martin Hellman in 1976.
2. RSA, invented in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman, is essentially the most generally used digital signature algorithm.
How Do Digital Signatures Work?
Digital signatures use a mixture of public key cryptography and hashing. The method usually includes the next steps:
- The entity sending the digital doc makes use of a personal key to create a hash of the doc, i.e., a fixed-length string of characters representing the doc’s contents.
- The sender then makes use of their personal key to encrypt the hash, creating the digital signature.
- The digital signature and the digitally signed doc are despatched to the recipient.
- The recipient makes use of the sender’s public key to decrypt the digital signature, and this offers them the unique hash of the doc.
- The recipient then makes use of the identical hash algorithm to create a brand new hash of the acquired doc.
- The recipient then compares the newly created hash with the decrypted hash from the signature; if each are the identical, it implies that the doc has not been tampered with.
- The sender’s public key can be used to confirm that the signature was created by the claimed sender and never an imposter.
On this method, digital signatures make sure the authentication and integrity of a digital doc, verifying that it has not been tampered with and was transmitted by the acknowledged sender. Therefore, a digital signature refers to a safer digital signature generated utilizing a digital certificates and cryptographically sure to the doc utilizing public key infrastructure (PKI).
Digital Signature in Blockchain
Digital signatures play an important position in establishing belief within the blockchain. In a blockchain community, transactions are grouped into blocks and added to a sequence of blocks in a linear, chronological order. Every block incorporates an inventory of transactions, together with a digital signature, referred to as a “hash,” that hyperlinks it to the earlier block within the chain.
This signature, referred to as a “nonce” is a quantity generated by the miner creating the block and is added to the block header, which is then hashed. The miner is looking for a nonce that may lead to a particular sample of main zeroes within the block hash.
All events utilizing digital signature expertise will need to have religion that the one that created the signature maintains the personal key secret. If malicious actors acquire entry to the personal key, they will forge digital signatures within the personal key holder’s title. Utilizing digital signatures together with PKI or PGP reduces the doable safety points related to transmitting public keys by validating that the important thing belongs to the sender and verifying the sender’s identification. The safety of a digital signature depends upon defending the personal key. Furthermore, with out PGP or PKI, proving somebody’s identification or revoking a compromised secret is unattainable.
Professional-Tip: Certificates Authorities (CAs), a kind of Belief Service Supplier, are broadly accepted as dependable organizations for making certain key safety and offering the required digital certificates. The certificates is used to verify that the general public key belongs to the particular group. Each the entity sending the doc and the recipient signing it should agree to make use of a given CA.
Digital Signatures in Bitcoin
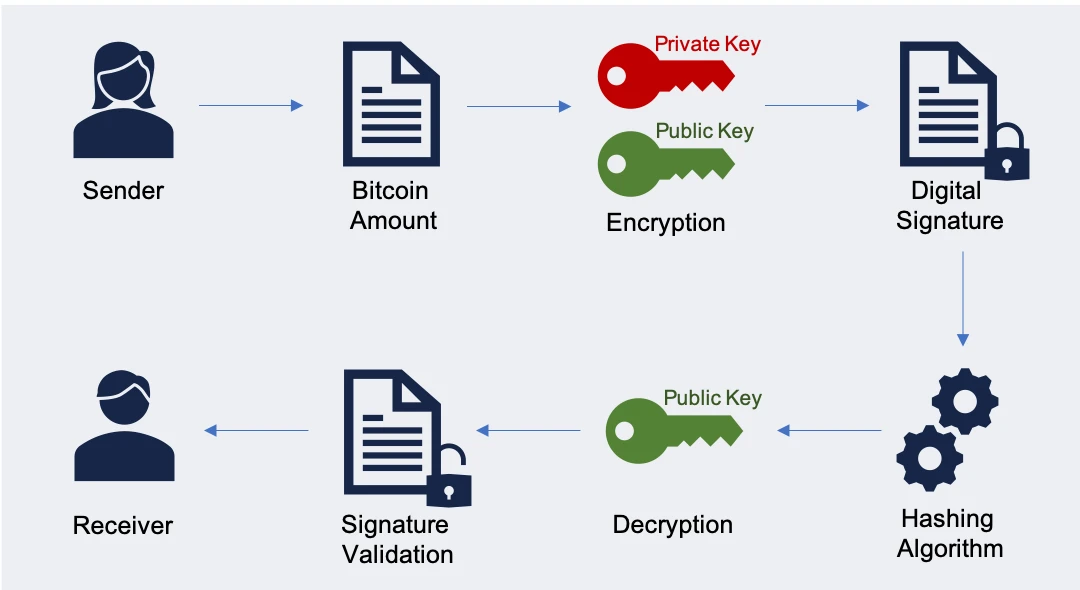
A digital signature in Bitcoin is a mathematical algorithm that makes use of cryptography to confirm the authenticity of a transaction. It permits a Bitcoin consumer to show they’re the proprietor of a selected public handle with authority to switch the funds related to that handle. Digital signatures in Bitcoin use the Elliptic Curve Digital Signature Algorithm (ECDSA) to generate a singular signature for every transaction. This signature is included within the transaction knowledge and is verified by different nodes within the community earlier than the transaction could be added to the blockchain.
For instance, if ‘X’ needs to switch ‘Y’ 1 bitcoin, X should signal a transaction utilizing its personal key and submit it to community nodes. Miners having the ‘X’ public key will then look at the transaction situations and validate the signature. When the legitimacy of a transaction is confirmed, the block containing that transaction is out there for finalization by a validator/miner.
What Is a Bitcoin Transaction?
A Bitcoin transaction is a switch of bitcoin from one handle to a different that’s recorded on the Bitcoin blockchain. It consists of a number of inputs and a number of outputs and features a digital signature to authorize the switch. The inputs specify the addresses and quantities of bitcoin being transferred, whereas the outputs specify the addresses and quantities of bitcoin being acquired. As soon as a transaction is included in a block that’s added to the blockchain, the transaction is confirmed, and the transferred bitcoins are thought of spendable.
How Do Bitcoin Transactions Work?
Let’s take the instance of Alice and Bob to be taught what occurs inside transactions and about cryptography utilization in Bitcoin.
The diagrams under depict Alice sending satoshis to Bob and Bob spending them. Alice and Bob will make the most of the most well-liked Pay-to-Public-Key-Hash (P2PKH) transaction sort. P2PKH permits Alice to ship satoshis to a regular Bitcoin handle and Bob to spend these satoshis utilizing a easy cryptographic key pair.
Later, Bob chooses to spend Alice’s UTXO:
Bitcoin Mining and Proof-Of-Work Consensus Mechanism
Bitcoins are generated by way of mining. To generate a block on the blockchain, a miner should clear up a fancy cryptographic downside, and the reply is a sequence of integers included inside the block often called the nonce. This methodology of figuring out the nonce is named Bitcoin mining and includes many miners worldwide.
Bitcoin mempool collects an unconfirmed transaction till it’s processed and added to the block. There are a number of mounted standards for the block, such because the earlier block hash, the traits of transactions within the present block, and many others. The nonce is the only real parameter that may be modified. The miner’s responsibility is to determine the nonce that may permit the candidate block to fulfill the problem goal. The one methodology to get the nonce is to aim a number of nonce values, compute the hash of the brand new block (final block hash id | block with transactions | nonce, the place ‘|’ signifies concatenate), and see if the hash meets the problem threshold (get a string that has a sure variety of zeros).
The miner’s duties are as follows:
Bitcoin’s Proof-of-Work consensus employs two successive SHA-256 hashes, the place the primary 32 of 256 hash bits should initially be zero. Nevertheless, the Bitcoin community modifications the problem stage usually to take care of the common tempo of block era at 10 minutes.
Digital Signatures vs. Digital Signatures
Digital signatures are a kind of digital signature used to signal paperwork and messages. A digital signature could be expressed digitally in digital kind and related to the illustration of a report. Whereas all digital signatures are digital signatures, the opposite shouldn’t be essentially true.
The important thing distinction between them is the authentication approach. Such cryptographic applied sciences as hash capabilities, public-key cryptography, and encryption strategies are utilized in digital signatures.
E-signatures are additionally outlined within the Digital Signatures Directive, which the European Union (EU) handed in 1999 and repealed in 2016. It regarded them as equal to bodily signatures. This act was changed with eIDAS (digital identification authentication and belief companies), which regulates e-signatures and transactions. eIDAS defines the three ranges of digital signatures: an digital signature (typically known as a “easy” signature), a sophisticated digital signature (AdES), and a certified digital signature (QES). AES provides identification verification, requiring signatures to be uniquely linked to the signatory and able to figuring out the signer. The signature report can present proof of tampering. QES requires face-to-face identification verification or the equal.
America handed the Digital Signatures in World and Nationwide Commerce Act (ESIGN) in 2000.
Many governments and companies additionally use sensible playing cards to ID their residents and staff.
What Are the Advantages of Digital Signatures?
Now that we’ve a normal concept of a digital signature, let’s study its benefits! The primary benefit of digital signatures is their safety. Digital signatures adjust to laws in lots of nations and supply the very best stage of identification assurance when coping with digital paperwork.
Digital signatures make use of the next safety traits and strategies:
- Private identification numbers (PINs), passwords, and codes. They’re used to determine and confirm a signer’s identification and validate their signature. The most typical use circumstances are e-mail, username, and password.
- Cyclic Redundancy Examine (CRC). An error-detecting code and verification operate used to detect modifications to uncooked knowledge in digital networks and storage units.
- Uneven Cryptography. A public key algorithm comprising a personal key and public key encryption and authentication.
- Certificates Authority (CA) Validation. CAs difficulty digital signatures and function a trusted third get together by accepting, verifying, issuing, and sustaining digital certificates. The usage of CAs support within the prevention of the fabrication of a cast digital certificates.
- Belief Service Supplier (TSP) Validation. A TSP is an individual or authorized entity that validates digital signatures on behalf of companies and supplies signature validation reviews.
- Traceability. Digital signatures create an audit path to simplify inner record-keeping for enterprises. There are fewer prospects for a guide signee or report keeper to make a mistake or misplace something when every little thing is recorded and saved digitally.
Closing Ideas
Digital signatures can present proof of the origin, identification, and standing of digital paperwork, transactions, or digital messages. Signers also can use them to acknowledge knowledgeable consent. The U.S. Authorities Publishing Workplace (GPO) publishes digital variations of budgets, private and non-private legal guidelines, and congressional payments with digital signatures.
Digital signatures are used within the blockchain to signal and approve Bitcoin transactions to make sure that cash are spent by individuals with the related personal keys.
Though we’ve been using digital and digital signatures for years, there may be nonetheless a lot area for enchancment. Whereas a big chunk of right now’s forms nonetheless makes use of paper paperwork, we’ll undoubtedly see better acceptance of digital signature strategies as we transition to a extra digitalized system.
You’re welcome to go to our CoinStats weblog to get a broader perspective on decentralized finance and the way it seeks to empower individuals. It’s also possible to learn our articles, akin to What Is DeFi, discover our in-depth shopping for and staking guides on numerous cryptocurrencies, akin to The way to Purchase Bitcoin, The way to Stake MATIC, The way to Stake Ethereum, The way to Purchase Cryptocurrency and be taught extra about wallets and exchanges, portfolio trackers, and many others.

